How to Track a Stolen Laptop: Complete Recovery Guide
Losing a device is scary, but speed, not panic, gets results. In the first minutes, focus on how to track a stolen laptop using built‑in tools, serial/MAC identifiers, and data‑protection steps. This guide strikes a balance between practical recovery and digital safety, enabling you to act quickly, avoid mistakes, and increase your chances of recovering the device.
Stay Calm, Confirm Loss, and Create a Paper Trail
Before you start technical tracking, establish facts. A clear head, a quick timeline, and proper documentation give you leverage with platforms, law enforcement, and insurers and help you avoid chasing false leads.
Retrace your path (home, office, café, transit). Ask staff or security to check the lost‑and‑found and CCTV. If theft is likely, file a police report immediately with brand, model, color, serial number, and photos. This report is essential when you track lost laptop leads, request platform takedowns, or claim insurance.
How to Track a Stolen Laptop with Built‑In Tools
Your fastest route is native tracking. Microsoft and Apple services can locate, lock, or erase the device, often within minutes, without extra software.
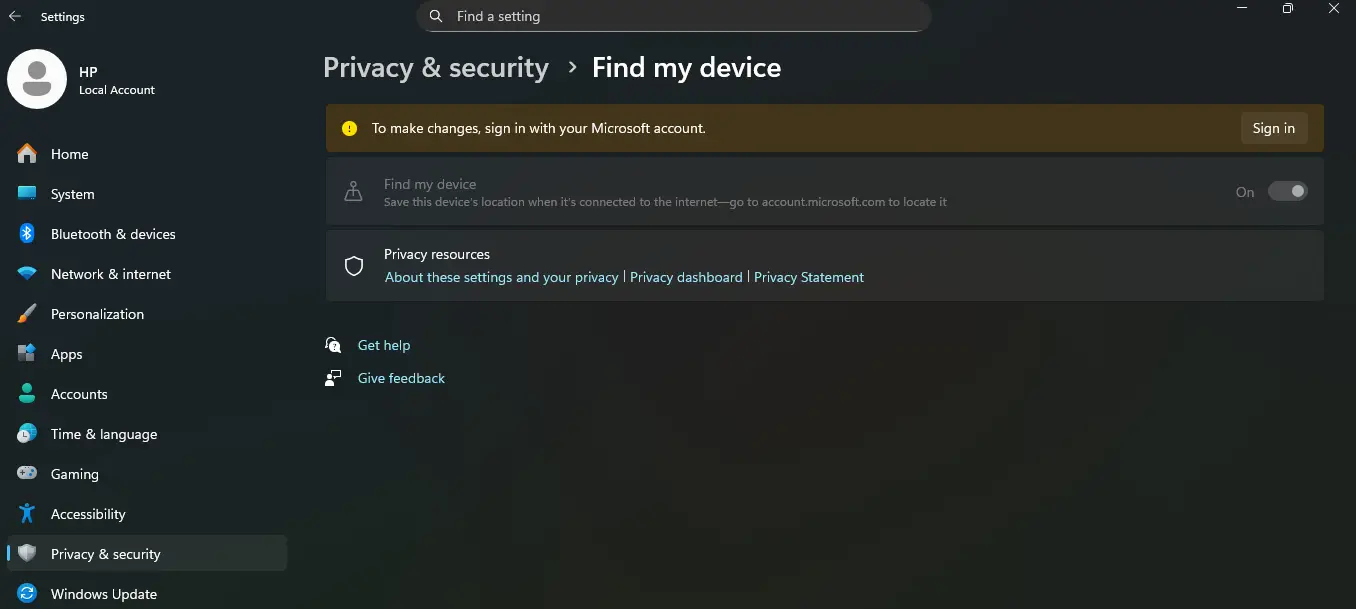
- Windows (Find My Device): Sign in at account.microsoft.com to see the last known location, play a sound, lock the device, show a return message, or erase it. Turn it on in Settings → Update & Security → Find My Device.
- macOS (Find My): Open the Find My app on another Apple device or visit iCloud.com. View location, Mark as Lost, display a message/number, or erase. Ensure Find My is enabled under Apple ID → iCloud → Find My Mac.

When you’re learning how to track a stolen laptop, act on each ping quickly: screenshot locations/timestamps, then share them only with authorities never confront a suspect yourself.
How to Track a Stolen Laptop with Serial Number or MAC Address
Identifiers don’t geolocate in real time, but they unlock official help. They prove ownership and surface the device during service, pawn, or resale checks.

- Serial number workflow (how to find a stolen laptop with a serial number): Keep photos of the box/receipt or check purchase emails, OEM portals, or your MDM/asset system. Provide the number to the police, your insurer, and the manufacturer so the unit can be flagged if it reaches service.
- MAC address: Find it from records, router logs, or MDM. Law enforcement can request ISP assistance to correlate IP activity to the device. Network admins at your office/campus can also look for last‑seen connections.
These steps won’t replace live tracking, but they reinforce claims and widen the net when you track a stolen laptop across repair shops and marketplaces.
Use IP Clues, Wi‑Fi History, and Network Logs (Advanced)
If native tools don’t resolve it, build a trail from connectivity breadcrumbs IP addresses, SSIDs, and timestamps that show where the laptop was online.
Check account security dashboards (Microsoft/Google/Apple) for new sign‑ins, IPs, and device activity. Save screenshots and times. Ask workplace/campus IT to review DHCP, RADIUS, or controller logs for the device hostname/MAC. These leads often complement built‑in pings when you track lost laptop sessions.
Secure Your Accounts and Data Immediately
Even if recovery takes time, you can stop the real damage from data theft. Locking down access protects your identity, contacts, and finances.

- Change passwords for email, cloud storage, banking, and work apps; invalidate old sessions.
- Enable MFA and check security alerts; remove unknown recovery methods.
- Remote lock/erase via Find My Device or Find My.
- Revoke tokens (Google/Microsoft/Okta) and log out of all browsers.
- If work data is involved, notify IT to trigger MDM wipe, DLP blocks, and incident response.
These steps belong in any plan for how to track a stolen laptop because they reduce harm while you investigate.
Scan Marketplaces and Start Official Requests
Many devices surface for sale within days. Systematic monitoring plus formal takedowns keeps the odds in your favor.
Search OLX, Quikr, and Facebook Marketplace using brand, model, specs, and unique stickers/engraving. Set saved searches and alerts. If you see a match, do not meet the seller. Send the listing, screenshots, and your report number to the police. Ask platforms for takedown or hold, citing the case number. This real‑world step is often how people find a lost laptop that’s moved into resale.
After You Get a Location, What’s Next?
Treat a live location as evidence, not a destination. Your safety comes first; authorities handle recovery.
Share precise coordinates/timestamps privately with the investigating officer. Bring proof of ownership (invoice, serial number, photos, device management records). If the device is recovered, image the drive before reuse (for forensics), then rotate all passwords/keys again.
Prevent It Next Time: Settings That Make Tracking Work
Preparation is the difference between recovery and regret. Ten minutes of setup now can save days of stress later.
- Enable Find My Device / Find My Mac and test that you can see the device online.
- Record identifiers: serial number, MAC address, asset tag; store in password manager.
- Encrypt the disk (BitLocker/FileVault) and use a strong login password.
- Turn on MFA for email, cloud, and password manager.
- Back up to OneDrive, iCloud Drive, or another cloud so data loss isn’t catastrophic.
- Consider a tracking/anti‑theft app (e.g., stealth camera, screenshots, location reports) where permitted.
All of these make it easier and faster when you need to track a stolen laptop again.
Quick Checklist: Track Lost Laptop Fast
Use this list when every minute counts.
- Confirm loss; file a police report with serial number and photos.
- Use Find My Device / Find My to locate, lock, or erase.
- Save screenshots of locations, IPs, and alerts.
- Notify work/IT; trigger MDM actions and revoke tokens.
- Monitor marketplaces; send leads to police don’t engage sellers.
Conclusion
Knowing how to track a stolen laptop means acting in layers native tools for fast pings, identifiers for official flags, and strict account security to limit damage. Pair methodical evidence collection with police coordination, and you maximize recovery odds while protecting your identity and work.
Need secure, business‑ready devices? At Rentopay, our rental laptops come with encryption, tracking readiness, and expert setup. Stay productive and prepared.
Ready to safeguard your workflow? Rent a secure laptop from Rentopay today in case of emergency and get a professional setup for tracking, encryption, and backups. We provide our services in popular cities like Bangalore, Mumbai, Delhi, Hyderabad, Gurgaon, Chennai, Pune, Noida, Kochi, Kolkata. Reach us immediately for best option.







